Software Defined Data Center (SDDC)
Software defined data center SDDC incorporates virtualized and logical computation, storage, networking resources, and other technologies with a standardized platform. For SDDC installation, ultra innovative and integrated infrastructure servers are being used. These resources are dynamically discovered, provisioned and configured, based on the demand of workload and usage.
Learn More
SD-WAN Networking Solution
The advancement of technology has transformed the way we work, requiring businesses to adopt modern software applications and IT infrastructure for efficient operations. With the development of digital platforms, companies can streamline their operations and enhance productivity, enabling them to stay ahead in a highly competitive market. These digital tools and technologies have also provided new opportunities for businesses to reach new customers and expand their market reach.
Learn More
Ship Local Area Network
The SLAN is a network designed for military and commercial grade ships, optimized to perform well in challenging marine situations with shock absorbent and high availability features. With a gigabit resilient network and hyper converged servers, it provides an effortless user experience and immediate response to outages. The built-in cyber secure system facilitates external data transmission over satellite and fiber-optical media.
Learn More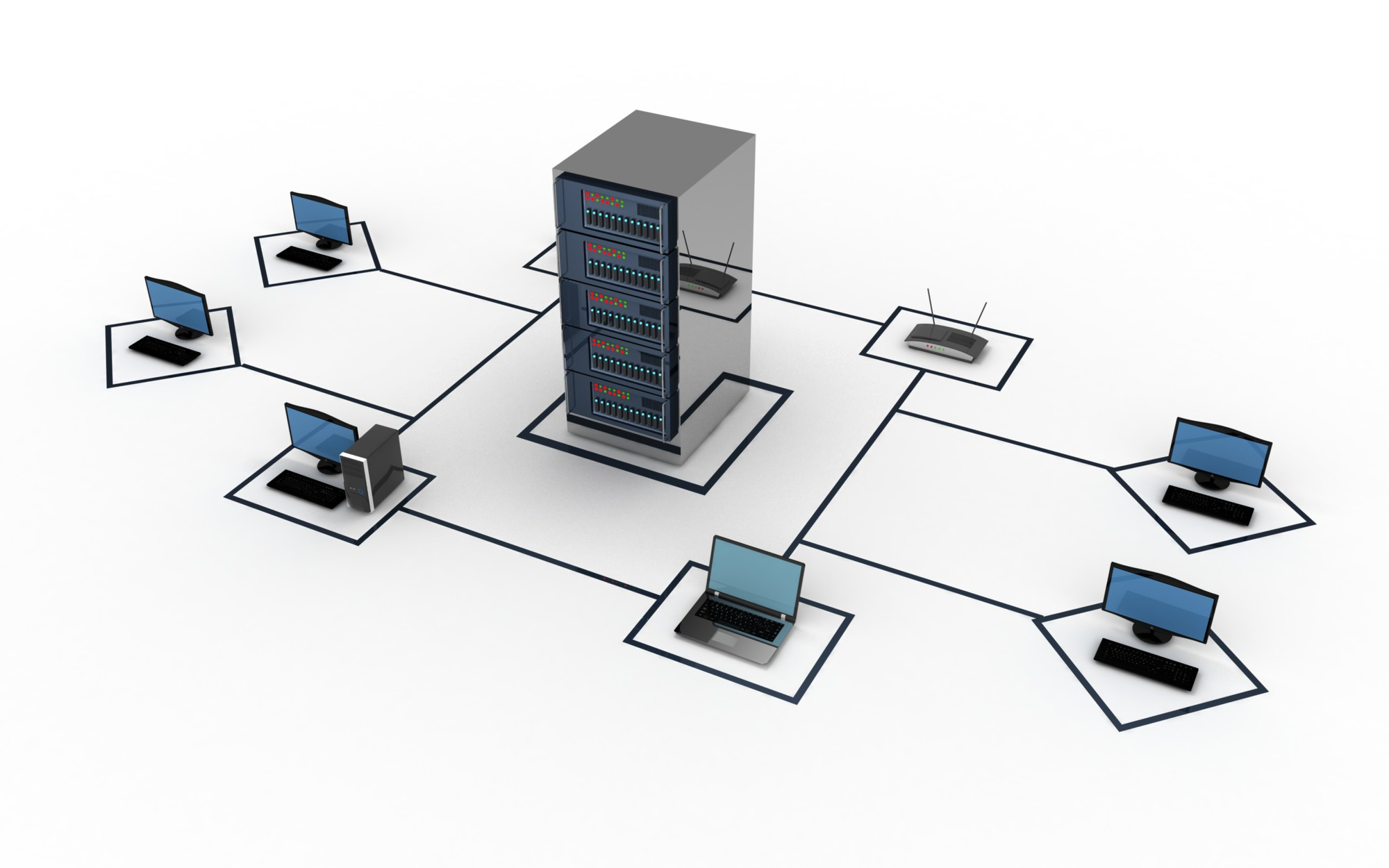
Cyber Security Solutions
In the current technological era, the risk of cyber attacks is increasing due to the rising online presence of businesses, making cybersecurity a critical priority. Various advanced techniques are employed to safeguard business-critical assets and globalized digital data worldwide. Stingray Technologies excels in protecting data and systems from all forms of cyber threats, including unauthorized access, use, disclosure, interception, and data damage.
Learn More